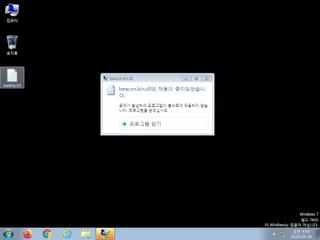
ScreenShot
| Created | 2025.04.28 09:12 | Machine | s1_win7_x6401 |
| Filename | beacon.bin | ||
| Type | PE32+ executable (DLL) (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 60 detected (AIDetectMalware, Malicious, score, cometer, Beacon, Marte, Unsafe, Save, confidence, 100%, CbltStrkT, DZHC, Windows, CobaltStrike, CobalStrike, CLASSIC, AGEN, Meterpreter, COBEACON, SMAC, Real Protect, moderate, Cobalt, Static AI, Malicious PE, Detected, XOREncoded, Eldorado, R325811, Artemis, GdSda, susgen, BeaconLoader) | ||
| md5 | b24faa9c6e485219f062a61daa9b205d | ||
| sha256 | 28f7f21d0ea33eff355cae889af64e37ae51252b5e345c3b98c95caae883bad0 | ||
| ssdeep | 6144:Gj/7Qsrm8pU99tkS1eTbqreronvFPedimOY:GvLPw9tZU+vFPeMNY | ||
| imphash | 46551b97c1d63fc258acfca97bdbeb94 | ||
| impfuzzy | 96:vosuVkCP+XX4w7SdmbvVjGHcpeStV/HMKKSx:A4ow5NDrt | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 60 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
Rules (10cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | CobaltStrike_IN | CobaltStrike | binaries (upload) |
| danger | HKTL_CobaltStrike_Beacon_Strings | Identifies strings used in Cobalt Strike Beacon DLL | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1800320b0 CreateNamedPipeA
0x1800320b8 TerminateProcess
0x1800320c0 CreateProcessA
0x1800320c8 GetCurrentDirectoryW
0x1800320d0 GetFullPathNameA
0x1800320d8 GetLogicalDrives
0x1800320e0 FindClose
0x1800320e8 SystemTimeToTzSpecificLocalTime
0x1800320f0 FileTimeToSystemTime
0x1800320f8 ExpandEnvironmentStringsA
0x180032100 GetFileAttributesA
0x180032108 FindFirstFileA
0x180032110 FindNextFileA
0x180032118 CopyFileA
0x180032120 MoveFileA
0x180032128 GetCurrentProcessId
0x180032130 CreateThread
0x180032138 CreateToolhelp32Snapshot
0x180032140 Thread32First
0x180032148 Thread32Next
0x180032150 Wow64GetThreadContext
0x180032158 Wow64SetThreadContext
0x180032160 VirtualAlloc
0x180032168 VirtualProtect
0x180032170 SetLastError
0x180032178 SetNamedPipeHandleState
0x180032180 PeekNamedPipe
0x180032188 CreateFileA
0x180032190 WaitNamedPipeA
0x180032198 GetModuleFileNameA
0x1800321a0 GetComputerNameA
0x1800321a8 GetVersionExA
0x1800321b0 GetACP
0x1800321b8 GetOEMCP
0x1800321c0 GetProcessHeap
0x1800321c8 InitializeProcThreadAttributeList
0x1800321d0 DeleteProcThreadAttributeList
0x1800321d8 SetErrorMode
0x1800321e0 UpdateProcThreadAttribute
0x1800321e8 ProcessIdToSessionId
0x1800321f0 Process32First
0x1800321f8 Process32Next
0x180032200 GetComputerNameExA
0x180032208 VirtualFree
0x180032210 VirtualQuery
0x180032218 VirtualAllocEx
0x180032220 VirtualProtectEx
0x180032228 OpenProcess
0x180032230 CreateRemoteThread
0x180032238 ConnectNamedPipe
0x180032240 ReadProcessMemory
0x180032248 WriteProcessMemory
0x180032250 GetThreadContext
0x180032258 SetThreadContext
0x180032260 ResumeThread
0x180032268 CloseHandle
0x180032270 DuplicateHandle
0x180032278 MapViewOfFile
0x180032280 UnmapViewOfFile
0x180032288 CreateFileMappingA
0x180032290 ExitProcess
0x180032298 ExitThread
0x1800322a0 ReadFile
0x1800322a8 GetCurrentThread
0x1800322b0 GetCurrentProcess
0x1800322b8 MultiByteToWideChar
0x1800322c0 GetCurrentDirectoryA
0x1800322c8 SetCurrentDirectoryA
0x1800322d0 GetStartupInfoA
0x1800322d8 DisconnectNamedPipe
0x1800322e0 CreatePipe
0x1800322e8 GetTickCount
0x1800322f0 GetLocalTime
0x1800322f8 FlushFileBuffers
0x180032300 WriteFile
0x180032308 WaitForSingleObject
0x180032310 Sleep
0x180032318 GetModuleHandleA
0x180032320 LoadLibraryA
0x180032328 GetLastError
0x180032330 HeapFree
0x180032338 RaiseException
0x180032340 SetEnvironmentVariableW
0x180032348 SetEnvironmentVariableA
0x180032350 HeapAlloc
0x180032358 HeapDestroy
0x180032360 HeapCreate
0x180032368 SetEndOfFile
0x180032370 CreateFileW
0x180032378 WriteConsoleW
0x180032380 SetStdHandle
0x180032388 GetStringTypeW
0x180032390 LCMapStringW
0x180032398 CompareStringW
0x1800323a0 HeapSize
0x1800323a8 LoadLibraryW
0x1800323b0 OutputDebugStringW
0x1800323b8 FreeEnvironmentStringsW
0x1800323c0 GetEnvironmentStringsW
0x1800323c8 QueryPerformanceCounter
0x1800323d0 RemoveDirectoryW
0x1800323d8 CreateDirectoryW
0x1800323e0 DeleteFileW
0x1800323e8 GetFileType
0x1800323f0 SetFilePointerEx
0x1800323f8 SetFilePointer
0x180032400 ReadConsoleW
0x180032408 GetConsoleMode
0x180032410 GetConsoleCP
0x180032418 WideCharToMultiByte
0x180032420 GetCPInfo
0x180032428 IsValidCodePage
0x180032430 RtlUnwindEx
0x180032438 GetProcAddress
0x180032440 OpenThread
0x180032448 FreeLibrary
0x180032450 EncodePointer
0x180032458 DecodePointer
0x180032460 GetModuleHandleExW
0x180032468 AreFileApisANSI
0x180032470 GetSystemTimeAsFileTime
0x180032478 HeapReAlloc
0x180032480 GetCommandLineA
0x180032488 GetCurrentThreadId
0x180032490 GetStdHandle
0x180032498 GetModuleFileNameW
0x1800324a0 IsDebuggerPresent
0x1800324a8 IsProcessorFeaturePresent
0x1800324b0 EnterCriticalSection
0x1800324b8 LeaveCriticalSection
0x1800324c0 InitializeCriticalSectionAndSpinCount
0x1800324c8 DeleteCriticalSection
0x1800324d0 RtlCaptureContext
0x1800324d8 RtlLookupFunctionEntry
0x1800324e0 RtlVirtualUnwind
0x1800324e8 UnhandledExceptionFilter
0x1800324f0 SetUnhandledExceptionFilter
0x1800324f8 TlsAlloc
0x180032500 TlsGetValue
0x180032508 TlsSetValue
0x180032510 TlsFree
0x180032518 GetStartupInfoW
0x180032520 GetModuleHandleW
0x180032528 LoadLibraryExW
ADVAPI32.dll
0x180032000 GetTokenInformation
0x180032008 OpenProcessToken
0x180032010 CryptReleaseContext
0x180032018 CryptAcquireContextA
0x180032020 CryptGenRandom
0x180032028 CheckTokenMembership
0x180032030 DuplicateTokenEx
0x180032038 LogonUserA
0x180032040 LookupAccountSidA
0x180032048 FreeSid
0x180032050 AllocateAndInitializeSid
0x180032058 ImpersonateNamedPipeClient
0x180032060 RevertToSelf
0x180032068 GetUserNameA
0x180032070 CreateProcessWithTokenW
0x180032078 CreateProcessWithLogonW
0x180032080 CreateProcessAsUserA
0x180032088 ImpersonateLoggedOnUser
0x180032090 LookupPrivilegeValueA
0x180032098 AdjustTokenPrivileges
0x1800320a0 OpenThreadToken
WININET.dll
0x180032538 InternetReadFile
0x180032540 InternetCloseHandle
0x180032548 InternetConnectA
0x180032550 InternetQueryDataAvailable
0x180032558 InternetQueryOptionA
0x180032560 InternetSetOptionA
0x180032568 InternetSetStatusCallback
0x180032570 HttpOpenRequestA
0x180032578 HttpAddRequestHeadersA
0x180032580 HttpSendRequestA
0x180032588 HttpQueryInfoA
0x180032590 InternetOpenA
WS2_32.dll
0x1800325a0 ntohs
0x1800325a8 gethostbyname
0x1800325b0 socket
0x1800325b8 send
0x1800325c0 connect
0x1800325c8 ioctlsocket
0x1800325d0 WSAIoctl
0x1800325d8 WSACleanup
0x1800325e0 WSAStartup
0x1800325e8 closesocket
0x1800325f0 ntohl
0x1800325f8 htons
0x180032600 htonl
0x180032608 recv
0x180032610 shutdown
0x180032618 WSAGetLastError
0x180032620 __WSAFDIsSet
0x180032628 accept
0x180032630 ind
0x180032638 inet_addr
0x180032640 listen
0x180032648 recvfrom
0x180032650 select
0x180032658 sendto
0x180032660 WSASocketA
EAT(Export Address Table) Library
0x1800194d4 ReflectiveLoader
KERNEL32.dll
0x1800320b0 CreateNamedPipeA
0x1800320b8 TerminateProcess
0x1800320c0 CreateProcessA
0x1800320c8 GetCurrentDirectoryW
0x1800320d0 GetFullPathNameA
0x1800320d8 GetLogicalDrives
0x1800320e0 FindClose
0x1800320e8 SystemTimeToTzSpecificLocalTime
0x1800320f0 FileTimeToSystemTime
0x1800320f8 ExpandEnvironmentStringsA
0x180032100 GetFileAttributesA
0x180032108 FindFirstFileA
0x180032110 FindNextFileA
0x180032118 CopyFileA
0x180032120 MoveFileA
0x180032128 GetCurrentProcessId
0x180032130 CreateThread
0x180032138 CreateToolhelp32Snapshot
0x180032140 Thread32First
0x180032148 Thread32Next
0x180032150 Wow64GetThreadContext
0x180032158 Wow64SetThreadContext
0x180032160 VirtualAlloc
0x180032168 VirtualProtect
0x180032170 SetLastError
0x180032178 SetNamedPipeHandleState
0x180032180 PeekNamedPipe
0x180032188 CreateFileA
0x180032190 WaitNamedPipeA
0x180032198 GetModuleFileNameA
0x1800321a0 GetComputerNameA
0x1800321a8 GetVersionExA
0x1800321b0 GetACP
0x1800321b8 GetOEMCP
0x1800321c0 GetProcessHeap
0x1800321c8 InitializeProcThreadAttributeList
0x1800321d0 DeleteProcThreadAttributeList
0x1800321d8 SetErrorMode
0x1800321e0 UpdateProcThreadAttribute
0x1800321e8 ProcessIdToSessionId
0x1800321f0 Process32First
0x1800321f8 Process32Next
0x180032200 GetComputerNameExA
0x180032208 VirtualFree
0x180032210 VirtualQuery
0x180032218 VirtualAllocEx
0x180032220 VirtualProtectEx
0x180032228 OpenProcess
0x180032230 CreateRemoteThread
0x180032238 ConnectNamedPipe
0x180032240 ReadProcessMemory
0x180032248 WriteProcessMemory
0x180032250 GetThreadContext
0x180032258 SetThreadContext
0x180032260 ResumeThread
0x180032268 CloseHandle
0x180032270 DuplicateHandle
0x180032278 MapViewOfFile
0x180032280 UnmapViewOfFile
0x180032288 CreateFileMappingA
0x180032290 ExitProcess
0x180032298 ExitThread
0x1800322a0 ReadFile
0x1800322a8 GetCurrentThread
0x1800322b0 GetCurrentProcess
0x1800322b8 MultiByteToWideChar
0x1800322c0 GetCurrentDirectoryA
0x1800322c8 SetCurrentDirectoryA
0x1800322d0 GetStartupInfoA
0x1800322d8 DisconnectNamedPipe
0x1800322e0 CreatePipe
0x1800322e8 GetTickCount
0x1800322f0 GetLocalTime
0x1800322f8 FlushFileBuffers
0x180032300 WriteFile
0x180032308 WaitForSingleObject
0x180032310 Sleep
0x180032318 GetModuleHandleA
0x180032320 LoadLibraryA
0x180032328 GetLastError
0x180032330 HeapFree
0x180032338 RaiseException
0x180032340 SetEnvironmentVariableW
0x180032348 SetEnvironmentVariableA
0x180032350 HeapAlloc
0x180032358 HeapDestroy
0x180032360 HeapCreate
0x180032368 SetEndOfFile
0x180032370 CreateFileW
0x180032378 WriteConsoleW
0x180032380 SetStdHandle
0x180032388 GetStringTypeW
0x180032390 LCMapStringW
0x180032398 CompareStringW
0x1800323a0 HeapSize
0x1800323a8 LoadLibraryW
0x1800323b0 OutputDebugStringW
0x1800323b8 FreeEnvironmentStringsW
0x1800323c0 GetEnvironmentStringsW
0x1800323c8 QueryPerformanceCounter
0x1800323d0 RemoveDirectoryW
0x1800323d8 CreateDirectoryW
0x1800323e0 DeleteFileW
0x1800323e8 GetFileType
0x1800323f0 SetFilePointerEx
0x1800323f8 SetFilePointer
0x180032400 ReadConsoleW
0x180032408 GetConsoleMode
0x180032410 GetConsoleCP
0x180032418 WideCharToMultiByte
0x180032420 GetCPInfo
0x180032428 IsValidCodePage
0x180032430 RtlUnwindEx
0x180032438 GetProcAddress
0x180032440 OpenThread
0x180032448 FreeLibrary
0x180032450 EncodePointer
0x180032458 DecodePointer
0x180032460 GetModuleHandleExW
0x180032468 AreFileApisANSI
0x180032470 GetSystemTimeAsFileTime
0x180032478 HeapReAlloc
0x180032480 GetCommandLineA
0x180032488 GetCurrentThreadId
0x180032490 GetStdHandle
0x180032498 GetModuleFileNameW
0x1800324a0 IsDebuggerPresent
0x1800324a8 IsProcessorFeaturePresent
0x1800324b0 EnterCriticalSection
0x1800324b8 LeaveCriticalSection
0x1800324c0 InitializeCriticalSectionAndSpinCount
0x1800324c8 DeleteCriticalSection
0x1800324d0 RtlCaptureContext
0x1800324d8 RtlLookupFunctionEntry
0x1800324e0 RtlVirtualUnwind
0x1800324e8 UnhandledExceptionFilter
0x1800324f0 SetUnhandledExceptionFilter
0x1800324f8 TlsAlloc
0x180032500 TlsGetValue
0x180032508 TlsSetValue
0x180032510 TlsFree
0x180032518 GetStartupInfoW
0x180032520 GetModuleHandleW
0x180032528 LoadLibraryExW
ADVAPI32.dll
0x180032000 GetTokenInformation
0x180032008 OpenProcessToken
0x180032010 CryptReleaseContext
0x180032018 CryptAcquireContextA
0x180032020 CryptGenRandom
0x180032028 CheckTokenMembership
0x180032030 DuplicateTokenEx
0x180032038 LogonUserA
0x180032040 LookupAccountSidA
0x180032048 FreeSid
0x180032050 AllocateAndInitializeSid
0x180032058 ImpersonateNamedPipeClient
0x180032060 RevertToSelf
0x180032068 GetUserNameA
0x180032070 CreateProcessWithTokenW
0x180032078 CreateProcessWithLogonW
0x180032080 CreateProcessAsUserA
0x180032088 ImpersonateLoggedOnUser
0x180032090 LookupPrivilegeValueA
0x180032098 AdjustTokenPrivileges
0x1800320a0 OpenThreadToken
WININET.dll
0x180032538 InternetReadFile
0x180032540 InternetCloseHandle
0x180032548 InternetConnectA
0x180032550 InternetQueryDataAvailable
0x180032558 InternetQueryOptionA
0x180032560 InternetSetOptionA
0x180032568 InternetSetStatusCallback
0x180032570 HttpOpenRequestA
0x180032578 HttpAddRequestHeadersA
0x180032580 HttpSendRequestA
0x180032588 HttpQueryInfoA
0x180032590 InternetOpenA
WS2_32.dll
0x1800325a0 ntohs
0x1800325a8 gethostbyname
0x1800325b0 socket
0x1800325b8 send
0x1800325c0 connect
0x1800325c8 ioctlsocket
0x1800325d0 WSAIoctl
0x1800325d8 WSACleanup
0x1800325e0 WSAStartup
0x1800325e8 closesocket
0x1800325f0 ntohl
0x1800325f8 htons
0x180032600 htonl
0x180032608 recv
0x180032610 shutdown
0x180032618 WSAGetLastError
0x180032620 __WSAFDIsSet
0x180032628 accept
0x180032630 ind
0x180032638 inet_addr
0x180032640 listen
0x180032648 recvfrom
0x180032650 select
0x180032658 sendto
0x180032660 WSASocketA
EAT(Export Address Table) Library
0x1800194d4 ReflectiveLoader