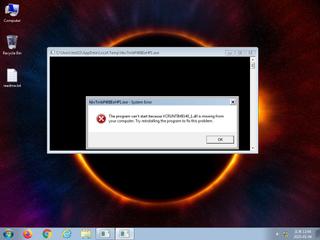
ScreenShot
| Created | 2025.05.04 13:13 | Machine | s1_win7_x6403 |
| Filename | hbvTmbP46IIEeHP1.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 41 detected (AIDetectMalware, CoinMiner, GenericKD, Unsafe, Save, malicious, confidence, 100%, Attribute, HighConfidence, high confidence, Themida, L suspicious, MalwareX, Misc, smehmm, Real Protect, high, score, Static AI, Malicious PE, Detected, Kepavll, ABTrojan, CQYK, Artemis, R002H01E325, susgen) | ||
| md5 | df316bf7fc49ebb8db6748ac07d54ba5 | ||
| sha256 | 27629e7de659a0c67d073ba155f97229b9f31d0b9a2797f24f6196615de49ef0 | ||
| ssdeep | 98304:utftYwaghIxulQullaedyxX5zujLOn6ocWwywq/n:PDvMCxX5b6ocewq/n | ||
| imphash | d85cf849818b3f831d8f001da4e76a11 | ||
| impfuzzy | 12:EJtbdRgBVDKaEtuFnUEx1W2Q4W2W4P1KQy4a6IMuD1FwBG:CxCMaEUs5bQ1tZIMu5FwBG | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 41 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | themida_packer | themida packer | binaries (upload) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
kernel32.dll
0x140028440 GetModuleHandleA
USER32.dll
0x140028450 GetShellWindow
ADVAPI32.dll
0x140028460 RegCloseKey
MSVCP140.dll
0x140028470 ??0?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
ntdll.dll
0x140028480 NtQuerySystemInformation
VCRUNTIME140_1.dll
0x140028490 __CxxFrameHandler4
VCRUNTIME140.dll
0x1400284a0 memcpy
api-ms-win-crt-stdio-l1-1-0.dll
0x1400284b0 _set_fmode
api-ms-win-crt-utility-l1-1-0.dll
0x1400284c0 srand
api-ms-win-crt-filesystem-l1-1-0.dll
0x1400284d0 _lock_file
api-ms-win-crt-string-l1-1-0.dll
0x1400284e0 _wcsicmp
api-ms-win-crt-time-l1-1-0.dll
0x1400284f0 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x140028500 _initialize_onexit_table
api-ms-win-crt-heap-l1-1-0.dll
0x140028510 _set_new_mode
api-ms-win-crt-locale-l1-1-0.dll
0x140028520 _configthreadlocale
api-ms-win-crt-math-l1-1-0.dll
0x140028530 __setusermatherr
EAT(Export Address Table) is none
kernel32.dll
0x140028440 GetModuleHandleA
USER32.dll
0x140028450 GetShellWindow
ADVAPI32.dll
0x140028460 RegCloseKey
MSVCP140.dll
0x140028470 ??0?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
ntdll.dll
0x140028480 NtQuerySystemInformation
VCRUNTIME140_1.dll
0x140028490 __CxxFrameHandler4
VCRUNTIME140.dll
0x1400284a0 memcpy
api-ms-win-crt-stdio-l1-1-0.dll
0x1400284b0 _set_fmode
api-ms-win-crt-utility-l1-1-0.dll
0x1400284c0 srand
api-ms-win-crt-filesystem-l1-1-0.dll
0x1400284d0 _lock_file
api-ms-win-crt-string-l1-1-0.dll
0x1400284e0 _wcsicmp
api-ms-win-crt-time-l1-1-0.dll
0x1400284f0 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x140028500 _initialize_onexit_table
api-ms-win-crt-heap-l1-1-0.dll
0x140028510 _set_new_mode
api-ms-win-crt-locale-l1-1-0.dll
0x140028520 _configthreadlocale
api-ms-win-crt-math-l1-1-0.dll
0x140028530 __setusermatherr
EAT(Export Address Table) is none